Daily Vulnerability Vendors Report - April 21, 2025
🔎 Summary: 3 vulnerabilities
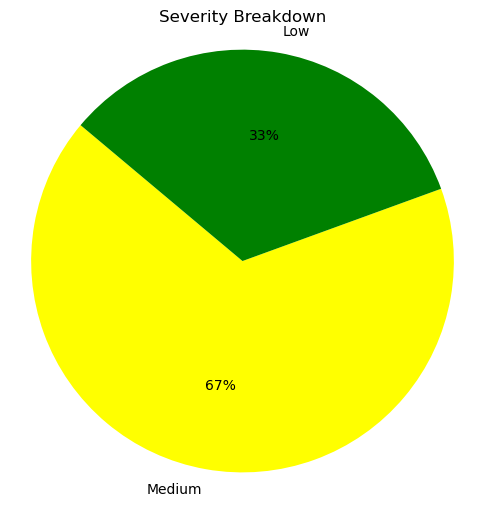
Severity breakdown:
🔴 0
🟠 0
🟡 2
🟢 1
❓ 0
Filtered vendors:
Cisco, Fortinet, Glpi-project, Microsoft, Palo Alto Networks, Splunk, Stormshield, Ubuntu Linux, VMware, Veeam, Wazuh
Vendors with vulnerabilities:
Splunk (3)
Page generated on Monday, April 21, 2025 at 02:40 PM
| ID | CVSS | EPSS | Vendor | Product | Description | Radar |
|---|---|---|---|---|---|---|
| EUVD-2025-8427 | 🟡 5.7 | 🔵 | Splunk | Splunk Enterprise, Splunk Cloud Platform | In Splunk Enterprise versions below 9.3.3, 9.2.5, and 9.1.8 and Splunk Cloud Platform versions below 9.3.2408.103, 9.2.2406.108, 9.2.2403.113, 9.1.2312.208 and 9.1.2308.212, a low-privileged user that... |  |
| EUVD-2025-8428 | 🟢 2.5 | 🔵 | Splunk | Splunk App for Lookup File Editing | In the Splunk App for Lookup File Editing versions below 4.0.5, a script in the app used the `chmod` and `makedirs` Python functions in a way that resulted in overly broad read and execute permissions... |  |
| EUVD-2025-8429 | 🟡 4.3 | 🔵 | Splunk | Splunk Enterprise, Splunk Secure Gateway | In Splunk Enterprise versions below 9.4.1, 9.3.3, 9.2.5, and 9.1.8, and versions below 3.8.38 and 3.7.23 of the Splunk Secure Gateway app on Splunk Cloud Platform, a low-privileged user that does not ... |  |
Legend:
CVSS Radar
- AV: Attack Vector (Network, Adjacent, Local, Physical)
- AC: Attack Complexity (Low, High)
- PR: Privileges Required (None, Low, High)
- UI: User Interaction (None, Required)
- S: Scope (Unchanged, Changed)
- C: Confidentiality Impact (None, Low, High)
- I: Integrity Impact (None, Low, High)
- A: Availability Impact (None, Low, High)
CVSS Severity
- 🔴 Critical (9.0 – 10.0)
- 🟠 High (7.0 – 8.9)
- 🟡 Medium (4.0 – 6.9)
- 🟢 Low (0.1 – 3.9)
- ❓ Unknown (0.0 or missing)
EPSS risk
- 🔴 High (0.5 - 1)
- 🟡 Medium (0.1 - 0.49)
- 🔵 Low (0.0 – 0.09)
EXPL Exploited in the wild
Definition:
- CVSS: Common Vulnerability Scoring System
- EPSS: Exploit Prediction Scoring System